01 Jan

Plesk is undoubtedly one of the leading web hosting control panels on the market in 2020. It offers a great range of features, while also featuring a great UI.
However, like any control panel it is paramount to manage Plesk Security to minimize the risk of being hacked.
Here we present the list of Highly Recommended Plesk Security features, both to be used by our clients and clients of other hosting companies. These recommendations have been tested and implemented by our team for many of our customers and have shown to have good resilience against attacks.
1. Web Application Firewall (WAF)
Web Application Firewall is a tool which blocks malicious requests to your website which seek to take advantage of web server vulnerabilities and get access to your server.
Plesk offers a wide range of WAF configurations, from free to Paid ones. The most basic configuration for you would be to turn on “Atomic Basic ModSecurity” ruleset which would prevent some of the most known attacks against your website.
There are also PAID WAF tools, like Atomicorp Paid version, which would need to be installed on your server. If the web server that you are running is CRITICAL, then it is highly recommended to use a PAID version of Atomicorp WAF.
It is perfectly integrated with Plesk and will cause no issues when accessing your website.
WAF configuration is available in:
“PLESK >> TOOLS >> SECURITY >> WEB APPLICATION FIREWALL”
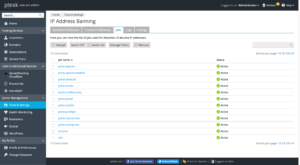
2. IP Address Banning
FAIL2BAN can be activated in Plesk to prevent automated Password brute-force attempts against many of Plesk services, such as SSH, Apache, FTP, Plesk, WordPress and more.
IP Address banning feature is also available in:
Plesk >> Tools >> Security >> IP Address Banning
We highly recommend to turn ON this feature when preparing your server for production deployment.
3. Spamassasin
By default Email Anti-Spam measures are DISABLED in Plesk and require manual setup.
You need to go to:
Plesk >> Tools >> Mail Server >> Spam Filter
Settings and activate Spamassasin on your server by clicking on:
Switch on server-wide SpamAssassin spam filtering
4. Web Server Hardening
There is a common attack type called “Remote File Execution” which happens when an attacker upload a malicious script on your website and it becomes possible for him to gain root access to the server.
By default, Plesk does Allow “Remote File Execution” feature and has no blocks against it.
We HIGHLY recommend disabling Remote File Execution to prevent such attacks in:
Plesk >> Service Plans >> select your service plan >> PHP Settings
then find: “disable_functions” and enter the following:
exec,passthru,shell_exec,system,proc_open
This will disallow remote file execution on your server and will prevent such attacks from happening.
5. Offsite Backups
We recommend keeping your Offsite Backups for added Plesk Security whenever possible.
Even if most anti-attack rules fail, you will still have a copy of your data.
It is critical to store backups Offsite, because in case of your server vulnerability, your data on the server, including local backups, may be corrupted.
Plesk supports multiple backup options which can and should be used.
6. Firewall
WooServers Cloud Instances allow you to setup a Firewall via Control Panel inside the Helpdesk.
One of the best options would be to DROP ALL non-legitimate traffic to PLESK via Firewall rules and ALLOW ACCESS only from your VPN or STATIC IP Address.
So, we would recommend a configuration, similar to this one:
VPN OR STATIC IP > ALLOW ALL INCOMING CONNECTIONS
Port 80 / 443 – ALLOW ALL INCOMING CONNECTIONS
Email Ports 25, 110, 143, 465 >>> ALLOW ALL INCOMING CONNECTIONS
DROP ALL OTHER INCOMING CONNECTIONS
Such rules will allow you to access ALL PLESK services via VPN or your own STATIC IP address and will limit everyone else to be able to access ONLY EMAIL and HTTP/S ports to browse websites on your server and serve email.
7. Anti-Virus
Plesk features a free anti-virus tool called IMUNIFY. We highly recommend enabling it to make sure your files are safe and secure.
8. WordPress Security
If you are running WordPress websites on Plesk, it is highly recommended to setup WORDPRESS SECURITY rules in WP Toolkit inside Plesk.
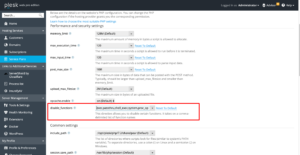
9. Password Strength Policy
If you allow 3rd party access to your Plesk, it is highly recommended to setup a HIGH Password Strength Policy so that users accessing your PLESK would be required to enter a Strong Password for authentication.
- Go to Tools & Settings > Security Policy (under “Security”), and then scroll down to the “Password strength” section.
- Under “Minimum password strength”, select the radio button corresponding to the desired password strength policy.
- Click OK.
10. Plesk Watchdog Service
Watchdog service is a tool that will continuously monitor your Plesk server and will restart services in case of failure. This may help you prevent DoS attacks against your services and will allow your server to automatically recover itself in case of critical issues.
Read more on Watchdog Service here: https://docs.plesk.com/en-US/12.5/deployment-guide/appendix-g-configuring-additional-plesk-components-linux/watchdog-system-monitoring-component.70443/
11. Enable Let’s Encrypt and Security Headers
Security Headers allow you to protect your websites from Cross-Site Scripting vulnerability attacks and are a required component of any server if you decide to sell services online and perform a PCI Standards Compliance procedure.
These are some of the most important Plesk Security Guidelines for the current moment. Feel free to post in comments your own recommendations.







Recent Comments